Trend Micro Endpoint Sensor (EDR)
Get more out of endpoint detection and response (EDR)

*Price per User, quantities 2-25
Our Price: $74.75
*Price per User, quantities 26-50
Our Price: $61.26
*Price per User, quantities 51-250
Our Price: $57.54
*Price per User, quantities 251+
Our Price: $56.32
Overview
Superior detection
Leverage a full portfolio of advanced detection techniques against an ever-growing variety of threats and targeted attacks. By integrating endpoint protection and EDR in a single agent, Trend Micro offers a comprehensive detection and response solution with automation and remediation capabilities.
XDR capabilities with Trend Micro
Take advantage of the options to extend endpoint detection and response capabilities to other security vectors, including email, servers, cloud workloads, and network and benefit from correlated detections and more insightful investigations.
Single view with integrated workflows
View detections, perform investigations, and initiate response from a single place for endpoints alone or across other Trend Micro security layers.
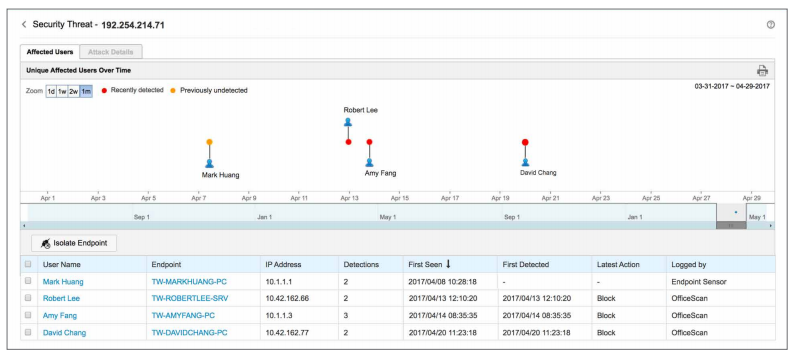
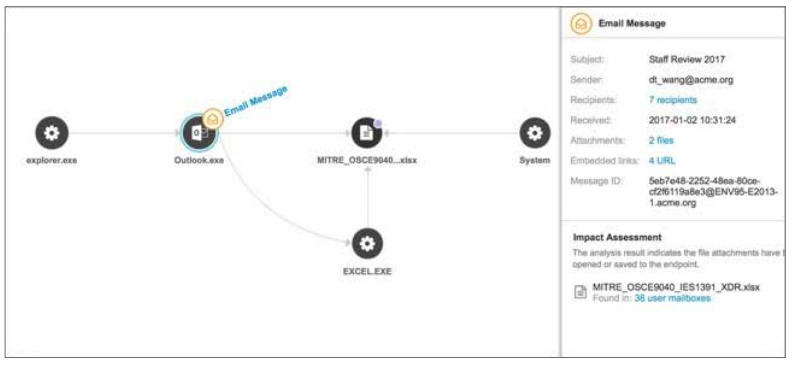
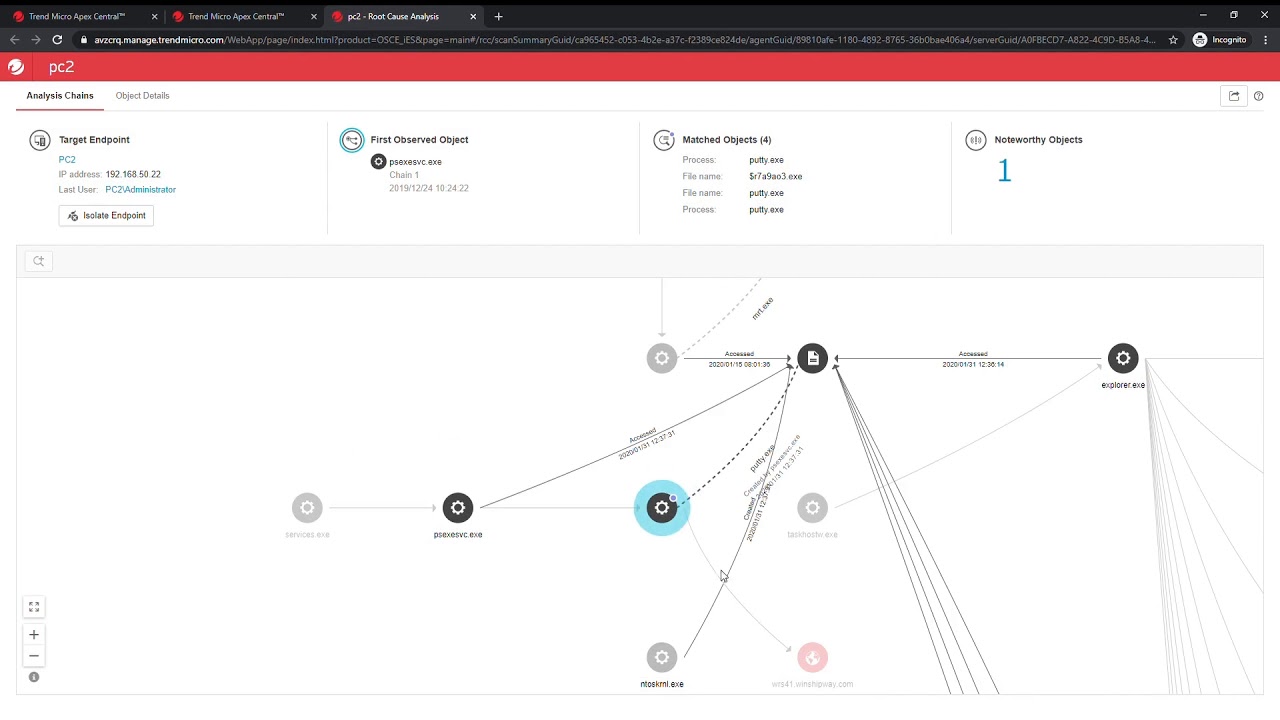
Root cause analysis and impact assessment
Get complete visibility into the attack vector, see the spread and extent of the impact of advanced threats. Incident response staff can quickly perform impact assessments, determine the root cause of the detection, and take proactive measures to remediate and update security.
Layering in global threat intelligence provides threat investigators with clarity, assistance, and a comprehensive database of threat information.
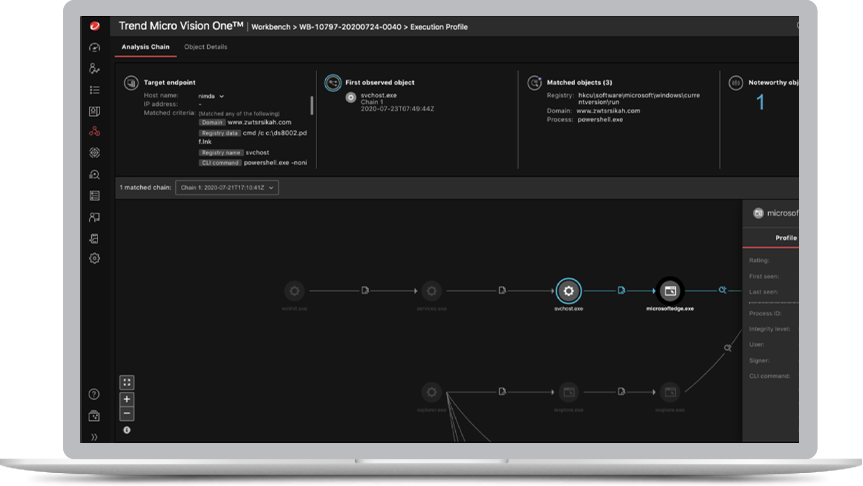
With Trend Micro EDR, endpoint analysis can be done in context of other security layers, empowering SOC and security analysts with a single source to run a root cause analysis, look at the execution profile of an attack (including associated MITRE ATT&CK TTPs), and identify the scope of impact across assets.
Sweeping and hunting
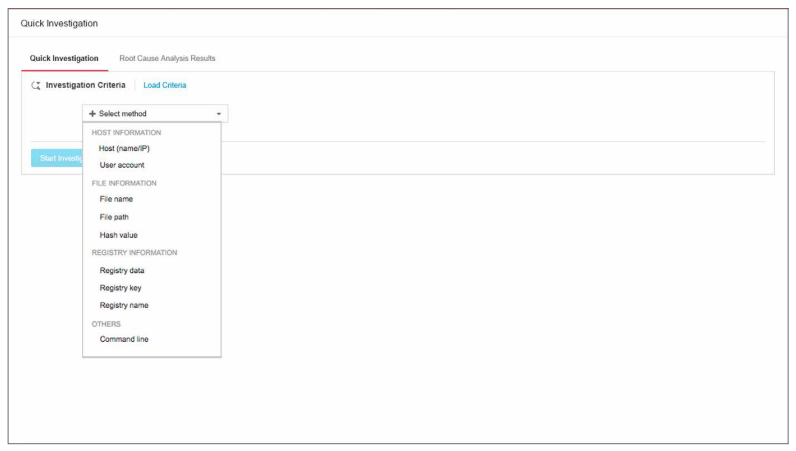
Perform multiple indicators of compromise (IoC) searches (or sweeping) with multiple parameters, like specific communications and malware, registry and account activity, and running processes.
Investigators can also search using industry standard OpenIoC or YARA rules and perform threat hunting based on indicators of attack (IoAs). This allows investigators to develop attack discovery rules or work with the IoAs provided by Trend Micro to hunt for threats.
By leveraging XDR across other Trend Micro solutions, analysts can sweep for IoCs or IoAs across the whole environment (messaging, endpoint, server, network) as a single action for a holistic view of which threats may reside within the enterprise.
Automated and integrated response
Isolate, quarantine, block executions, roll back settings (and files, in the case of ransomware), with the option for investigators to also manually respond while performing an investigation. Endpoints can be isolated, processes can be terminated, and security intelligence can be automatically updated on a per-user or enterprise-wide basis.